mirror of
https://github.com/safing/web
synced 2025-09-02 11:09:03 +00:00
Merge pull request #93 from safing/feature/retext-blogs
Feature/retext blogs
This commit is contained in:
commit
cde6769abd
18 changed files with 238 additions and 114 deletions
|
|
@ -5,7 +5,7 @@
|
|||
<div class="block lg:flex items-center py-5">
|
||||
<input style="background-color: #302e37;" type="email" name="email" class="appearance-none rounded-full w-full max-w-md px-6 py-2 text-white focus:outline-none" required placeholder="email">
|
||||
<div class="pt-5 lg:pt-0 lg:pl-5 ">
|
||||
<input type="submit" value="Subscribe" style="background-color: #6188ff;" class="transform hover:scale-95 inline-flex items-center px-10 py-3 border border-transparent text-xs leading-5 font-extrabold rounded-full text-white hover:bg-indigo-500 focus:outline-none focus:border-indigo-700 active:bg-indigo-700 transition duration-150 ease-in-out uppercase" />
|
||||
<input type="submit" value="Subscribe" style="background-color: #6188ff;" class="cursor-pointer transform hover:scale-95 inline-flex items-center px-10 py-3 border border-transparent text-xs leading-5 font-extrabold rounded-full text-white hover:bg-indigo-500 focus:outline-none focus:border-indigo-700 active:bg-indigo-700 transition duration-150 ease-in-out uppercase" />
|
||||
</div>
|
||||
</div>
|
||||
<div class="max-w-md flex">
|
||||
|
|
@ -67,6 +67,9 @@
|
|||
<li class="mt-2 inline-block mr-2 md:block md:mr-0">
|
||||
<a href="{{ site.blog_url }}" class="no-underline hover:opacity-100 opacity-55 text-white transition duration-150 ease-in-out">Blog</a>
|
||||
</li>
|
||||
<li class="mt-2 inline-block mr-2 md:block md:mr-0">
|
||||
<a href="{{ site.next_page_url }}" class="no-underline hover:opacity-100 opacity-55 text-white transition duration-150 ease-in-out"> What's Next?</a>
|
||||
</li>
|
||||
</ul>
|
||||
</div>
|
||||
<div class="flex-1">
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
<div class="card text-left transform scale-95">
|
||||
<div class="block shadowthing p-8 rounded-lg">
|
||||
<div class="block cardshadow p-8 rounded-lg">
|
||||
<div class="tabs">
|
||||
<div class="tab">
|
||||
<input class="dropinput" type="checkbox" id="card-{{ include.state }}-{{ forloop.index }}">
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
<div class="tablecard shadowthing text-left transform scale-95">
|
||||
<div class="block px-8 py-6 rounded-lg">
|
||||
<div class="tablecard cardshadow text-left transform">
|
||||
<div class="block px-8 py-6 rounded-lg">
|
||||
<div class="absolute top-0 right-0 overflow-visible mr-16 mt-12 z-20">
|
||||
<div class="flex-shrink-0 mt-0">
|
||||
<div class="flex ">
|
||||
|
|
@ -54,7 +54,7 @@
|
|||
<img style="min-width: 19px;" src="{{ site.assets_url }}icons/files.svg" alt="">
|
||||
{% endif %}
|
||||
</div>
|
||||
<h1 class="pl-3 font-bold text-lg">{{ card.title }}</h1>
|
||||
<h1 class="pl-3 font-bold text-lg pr-16 ">{{ card.title }}</h1>
|
||||
</div>
|
||||
</div>
|
||||
</div>
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
<li class="list-none mt-10 md:mt-0">
|
||||
<div class="block transform hover:scale-95 duration-150 ease-in-out">
|
||||
<li class="list-none mt-10 md:mt-0 grid">
|
||||
<div class="block transform hover:scale-95 duration-150 ease-in-out" style="max-width: 350px; justify-self: center;">
|
||||
<a href="{{ post.url }}">
|
||||
<div class="relative" style="max-width: 365px;">
|
||||
{% if post.custom_thumbnail_name == null %}
|
||||
|
|
|
|||
|
|
@ -4,10 +4,10 @@ layout: page
|
|||
|
||||
<section id="page-container" class="pb-8 lg:pb-24 pt-16 lg:pt-40 {{ layout.container_class }} {{ page.container_class }}">
|
||||
<div class="items-center h-full">
|
||||
<div class="container mx-auto px-8 sm:px-0 flex">
|
||||
<div class="container mx-auto sm:px-8 sm:px-0 flex">
|
||||
<div class="max-w-screen-lg mx-auto px-4 sm:px-6 lg:flex">
|
||||
<div class="py-12 bg-white">
|
||||
<div class="max-w-screen-xl mx-auto px-4 sm:px-6 lg:px-8">
|
||||
<div class="max-w-screen-xl mx-auto px-2 sm:px-6 lg:px-8">
|
||||
<content>
|
||||
{% unless page.heading == null %}
|
||||
<h1 class="text-5xl tracking-tight font-extrabold leading-none">
|
||||
|
|
|
|||
|
|
@ -21,7 +21,7 @@ layout: page_container
|
|||
{% if page.progress_update %}
|
||||
<div>
|
||||
{% else %}
|
||||
<div class="content">
|
||||
<div class="content" id="blog">
|
||||
{% endif %}
|
||||
{{ content | replace: '<!--break-->', '<a class="anchor" id="continue"></a>' }}
|
||||
</div>
|
||||
|
|
|
|||
|
|
@ -8,41 +8,41 @@ cover_image_source: https://unsplash.com/photos/66O6CE7QvwI
|
|||
|
||||
_Sidenote: shoutout to [The Hated One](https://www.youtube.com/channel/UCjr2bPAyPV7t35MvcgT3W8Q/), this would not have happened without him!_
|
||||
|
||||
## The Grant
|
||||
## First, We Applied for a Big Grant
|
||||
|
||||
Back in June we applied for our biggest grant so far. If it was successful, we would receive a grant of around 160.000€ with an additional 150.000€ loan which we would need to pay back in the next years. This meant - with over 300K to work with - we could hire our first employees, pay a code audit, pay our lawyer and even pay us founders our first salaries - which we'd see as a very welcome change indeed. So after weeks and months of preparation and work, on the 5th of June 2019 we sent off our application.
|
||||
|
||||
## The long Wait
|
||||
## A Long and Uncertain Wait
|
||||
|
||||
So off it went, and even though finishing an application was relieving, we knew this did not mean much. It was only a _chance_ of getting this money. And on top of that, we knew we would have to wait until September to get the notice. So we still had to count with a negative and it was with this mentality we went into the next few months.
|
||||
|
||||
## The Gamble
|
||||
## We Decided to Gamble
|
||||
|
||||
Then August came around. We were invited to an official review of our application. This meant we made it to the second round - 🎉 (but still no certainty). In the application we already mentioned we would hire three employees, but only one of them we already had a candidate for. As a result, they told us *if* we received the grant, we would have to fill one of the positions until they would send us the first batch. Hiring is no easy feat, and we were beginners at that. Was it worth taking the risk of investing a lot of hours into hiring a person if we may not even get the grant in the end? We would waste our time and the time of applicants. We made a leap of faith and just went for it.
|
||||
|
||||
## Hiring rounds
|
||||
## The Hiring Process Starts
|
||||
|
||||
The next days I worked on our job description. A big shoutout to ghost.org - [their style and structure](https://careers.ghost.org/visual-designer/en) was great inspiration! After we distributed it through a few channels we for a responses. [Raphael]({{ site.team_url }}) pre-filtered many of the applications and with a few we set up a video call. The grant was restricted to Austria 🇦🇹, so even though we are open for remote workers, this position needed to be filled anywhere in Austria.
|
||||
The next days I worked on our job description. A big shoutout to ghost.org - [their style and structure](https://careers.ghost.org/visual-designer/en) was great inspiration! After we distributed it through a few channels we for a responses. Raphael pre-filtered many of the applications and with a few we set up a video call. The grant was restricted to Austria 🇦🇹, so even though we are open for remote workers, this position needed to be filled anywhere in Austria.
|
||||
|
||||
It was fun getting to dive into this area from an employers perspective. So far we've only sat on the other side of the table. One thing I learned was that you really get much more interested if an application sticks out from standard, generic descriptions. And then in our situation you _really_ stick out if you are already into privacy and burning for our mission. We had two applicants who restricted their work to _only_ privacy projects. One of them could not move to Austria, which was a dealbreaker, and the other one was Luke.
|
||||
|
||||
## Luke
|
||||
## Then Luke Appeared on the Scene
|
||||
|
||||
_Sidenote: [Luke talks all about his side of the story in the podcast]({{ site.podcast_url }}2019/11/29/hiring-a-designer-from-the-privacy-community/)_
|
||||
|
||||
From the very first email we received from Luke we learnt two things: he burns for privacy and he is outspoken. This was even more affirmed after [Raphael]({{ site.team_url }}) and I got to know him via a video call (Luke's from the United Kingdom).
|
||||
From the very first email we received from Luke we learnt two things: he burns for privacy and he is outspoken. This was even more affirmed after Raphael and I got to know him via a video call (Luke's from the United Kingdom).
|
||||
|
||||
The even crazier thing about this was, Luke found out about us and the job via The Hated One. I appeared on [his channel twice](https://www.youtube.com/channel/UCjr2bPAyPV7t35MvcgT3W8Q/), but would never have thought that this would end up helping us hiring our designer. HUGE shoutout to THO!!!
|
||||
|
||||
After plenty of interviews and rounds we had the two most promising candidates remaining. The other applicant lived nearby, so we could meet in person, but Luke we only meat digitally.
|
||||
|
||||
## Flying him in
|
||||
## Flying Him In
|
||||
|
||||
Since it's easy to pull off a show for a few hours online, we really wanted to get to know Luke in person before making our decision. We offered him to fly in over the weekend, which he accepted after some suspicion.
|
||||
|
||||
We booked the flight the day before we received the result about the grant, which increased the gamble, but hey: [the next day we got it]({{ site.ownership_url }}#influences) 🎉
|
||||
|
||||
## His weekend in Austria
|
||||
## His Weekend in Austria
|
||||
|
||||
The weekend was very fun! For me at least - I know Luke rather very nervous in the beginning. He arrived Friday evening, and all of us met on Saturday for lunch at a pizza place. Luke accidentally ordered a pizza, which turned out to be rather complicated to eat, which made him stress out even more. Imagine his situation: You're going to an interview for a job you're excited about. You know you and another candidate are the only ones left. And then all three founders and you go grab some lunch. All eyes on you - and then you're having troubles eating your pizza.
|
||||
|
||||
|
|
@ -52,11 +52,11 @@ Luke had to be sure about this too, since it meant he would have to move to anot
|
|||
|
||||
The next day we dropped him off at the airport. And that Sunday evening all involved knew: the big decision would be made the next day.
|
||||
|
||||
## The decision
|
||||
## His Burning for Privacy Was the Dealbreaker
|
||||
|
||||
It is rather obvious by now that we decided to hire Luke. But both candidates were promising: both had strengths and weaknesses in different areas and both were outspoken. Being blunt turns out to be especially helpful when us founders are rather hardheaded. So what was the dealbreaker? **Luke is burning for privacy.** He has a personal privacy project which [you should check out too](https://latestprivacy.org/).
|
||||
It is rather obvious by now that we decided to hire Luke. But both candidates were promising: both had strengths and weaknesses in different areas and both were outspoken. Being blunt turns out to be especially helpful when us founders are rather hardheaded. So what was the dealbreaker? Luke is burning for privacy. He has a personal privacy project which [you should check out too](https://latestprivacy.org/).
|
||||
|
||||
## His work so far
|
||||
## Starting out in Austria
|
||||
|
||||
It took Luke a few weeks to pack up his things and move to Austria, but soon enough, at the beginning of October he became our lead designer. We are very grateful for his work so far and see him as a perfect fit for the job.
|
||||
|
||||
|
|
@ -64,7 +64,7 @@ He made us reconsider [our old designs]({{ site.img_url }}/archive/previous_desi
|
|||
|
||||
_Sidenote: [Luke talks all about his side of the story in the podcast]({{ site.podcast_url }}2019/11/29/hiring-a-designer-from-the-privacy-community/). Also, you can [follow him on Twitter.](https://twitter.com/LukeSeers/)_
|
||||
|
||||
## Wrap up
|
||||
## Wrap Up
|
||||
|
||||
Again, this would not have been possible without [The Hated One](https://www.youtube.com/channel/UCjr2bPAyPV7t35MvcgT3W8Q/)! It was a pleasure talking to him and if you don't know him already, check out his videos. They're a great resource for privacy and related topics.
|
||||
|
||||
|
|
|
|||
|
|
@ -1,12 +1,12 @@
|
|||
---
|
||||
title: The next 5 steps for Safing
|
||||
title: The next 5 Steps for Safing
|
||||
date: 2019-12-06
|
||||
author: davegson
|
||||
custom_thumbnail_name: the-next-5-steps-for-safing
|
||||
cover_image_source: https://pixabay.com/photos/architecture-stone-blocks-block-3481302/
|
||||
---
|
||||
|
||||
## Intro
|
||||
## A Rough Estimate of What Might Happen in 2020
|
||||
|
||||
With our Kickstarter around the corner - launching on the 2nd of January 2020 - we thought this might be a good time to communicate what our next steps are going to be. These are no far fetched, crazy dreams, but instead executable plans. In 2020, we will surely finish several of these steps. And if the campaign goes well enough, we could gain sufficient resources to hire additional talent, helping us complete them all!
|
||||
|
||||
|
|
@ -38,7 +38,7 @@ As we already intercept your connections, why not enable you to block the faulty
|
|||
|
||||
And the best it will be totally free to use. We totally get that not everyone will be able to pay for the SPN and its servers - but why not enable them to get stealthy privacy too? There is no reason not to!
|
||||
|
||||
## Stage 1. completed & future plans
|
||||
## Our Dream for Stage 1. and further Plans
|
||||
|
||||
That will complete the first stage of our plans. At this point we can finally give away an open source, powerful application firewall. Free for anyone to use, supporting all desktop operating systems. And those who like what we do and can afford it, can then pay for the SPN to support us. We truly cannot wait!
|
||||
|
||||
|
|
|
|||
|
|
@ -5,30 +5,29 @@ author: davegson
|
|||
custom_thumbnail_name: announcing-the-privacytools-sponsorship
|
||||
---
|
||||
|
||||
**We are very pleased to announce that we have become a sponsor of [PrivacyTools.io](https://opencollective.com/privacytoolsio)**
|
||||
**Today we announce that we have become a sponsor of [PrivacyTools.io](https://opencollective.com/privacytoolsio)**
|
||||
|
||||
We are delighted to be in a position where we are able to share our resources, and equally enthusiastic that we can start this off by supporting the amazing team behind the PrivacyTools venture.
|
||||
We are delighted to be in a position where we are able to share our resources, and equally enthusiastic that we can start this off by supporting the amazing PrivacyTools venture.
|
||||
|
||||
## What is PrivacyTools?
|
||||
|
||||
[PrivacyTools](https://privacytools.io) is an endeavor which strives to inform, educate and empower privacy-minded people to withstand today's mass surveillance. Their thriving community members do not only help each other out, but also equip and aid all newcomers into the field. The team's openness in all their decision making, criteria and finances continues to validate their gained trust across the privacy scene. If you are able [to spare time](https://www.privacytools.io/index.html#participate) or [money](https://www.privacytools.io/donate/), we encourage you to support them too!
|
||||
|
||||
## Their Work Impacted Us Personally
|
||||
|
||||
## First, we received
|
||||
Before the Safing venture started, the work of PrivacyTools already impacted all three of us founders. Their website helped us in numerous ways. Whether to deepen our understanding of the importance of privacy or about arguments we can make for it. And most importantly, their software recommendations and instructions armed us to better fight today's mass surveillance. I fondly remember the first time I proudly configured my `about:config` of Firefox, enthusiastically heading to the next section to install additional privacy enhancing extensions.
|
||||
|
||||
Before our whole venture happened, before we came to this point, the work of PrivacyTools already impacted all three of us founders. Their website helped us in numerous ways. Whether to deepen our understanding of the importance of privacy or about arguments we can make for it. And most importantly, their software recommendations and instructions armed us to better fight today's mass surveillance. I fondly remember the first time I proudly configured my `about:config` of Firefox, enthusiastically heading to the next section to install additional privacy enhancing extensions.
|
||||
## Sharing is Caring
|
||||
|
||||
## Sharing is caring
|
||||
|
||||
Being into the Safing venture for more than two years, it's amazing having a look back and realizing how far we have come. But at the same time it's also humbling to see how much of it cannot be credited to us, but instead to others. Fellow travelers, founders or privacy advocates - all generously shared their time and input to help us grow. They pushed us to rethink our strategies, gave valuable input on our designs or even gave us a platform where our voices were heard.
|
||||
Being into our venture for more than two years, it is amazing having a look back and realizing how far we have come. But at the same time it's also humbling to see how much of it cannot be credited to us, but instead to others. Fellow travelers, founders or privacy advocates - all generously shared their time and input to help us grow. They pushed us to rethink our strategies, gave valuable input on our designs or even gave us a platform where our voices were heard.
|
||||
|
||||
Shorty after receiving a big grant from the Austrian Institution for Research, PrivacyTools presented their sponsorship program via Github. Excitedly, I knew the time had come for us to start sharing our received resources with fellow privacy advocates. We decided this while fully being aware that this might fuel our venture too, or it might not - that's for every reader of this announcement to decide. But to us, that is not a dealbreaker. In either case we are happily supporting a genuine and caring team!
|
||||
|
||||
## The Evaluation Process
|
||||
## We Got Vetted via Chat
|
||||
|
||||
After reaching out to the team, we were invited to a team chat to discuss everything further. Being listed as a sponsor is completely decoupled from their software recommendations, but still both parties wanted to get to know each other beforehand. As their team is spread across the whole globe, the chat spanned a few days, asynchronously. It was a very encouraging experience to meet and get to know fellow travelers, who are just as committed to the cause of privacy as we are. If you want to meet the team or other fellow privacy enthusiasts, feel free to [hop onto their chat](https://chat.privacytools.io/) ;) - it's a great place to hang out.
|
||||
After reaching out to the team, we were invited to a team chat to discuss everything further. Being listed as a sponsor is completely decoupled from their software recommendations, but still both parties wanted to get to know each other beforehand. As their team is spread across the whole globe, the chat spanned a few days, asynchronously. It was a very encouraging experience to meet and get to know fellow travelers, who are just as committed to the cause of privacy. If you want to meet the team or other fellow privacy enthusiasts, feel free to [hop onto their chat](https://chat.privacytools.io/) ;) - it's a great place to hang out.
|
||||
|
||||
## Wrap up
|
||||
## Privacy Space, Unite!
|
||||
|
||||
Just as mentioned in [the accompanying podcast](https://safing.io/podcast/2019/12/20/becoming-privacytools-first-sponsor/), I really feel the privacy space is maturing. We are not only growing in numbers, but we are also growing tighter together. It is a great community, where one thing is allowed to fuel the other, all here to support one another. We are really hopeful that the 20s will be the decade where we take back our right to privacy. And you can count on Safing to play its part, not only with some kickass software, but also by supporting more and more projects which strive for the same utopia as all of us.
|
||||
|
||||
|
|
|
|||
|
|
@ -5,44 +5,29 @@ author: davegson
|
|||
custom_thumbnail_name: spn-tor
|
||||
---
|
||||
|
||||
## Different Missions
|
||||
## Tor's Mission is Broad, Safing Focuses on Easy of Use
|
||||
|
||||
**Tor project's mission**
|
||||
|
||||
from [https://www.torproject.org/](https://www.torproject.org/) - in the footer
|
||||
Tor's mission statement (from [https://www.torproject.org/](https://www.torproject.org/) - in the footer), declares:
|
||||
|
||||
> To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.
|
||||
|
||||
**Safing's mission**
|
||||
We wholeheartedly agree and appreciate Tor's work and outlined broader mission, but our focus is on a specific sub-area of theirs:
|
||||
|
||||
from [https://safing.io/our-values/](https://safing.io/our-values/)
|
||||
We believe that freedom can only flourish when privacy is the default. And privacy will only be broadly adopted if it is easy to use. So "Easy to use" is our focus: we want my mom and your mom to be able to conveniently withstand mass surveillance without having to venture deep into tech. This is what drives us. This is our mission.
|
||||
|
||||
> Enabling you to reclaim your privacy
|
||||
> We're building tools to help everyone withstand today's mass surveillance
|
||||
|
||||
**A comparison**
|
||||
|
||||
How would you differentiate them?
|
||||
|
||||
My take is that Tor's mission is broader than ours. They do overlap, in the sense that one can interpret their mission to include ours. We wholeheartedly agree and appreciate Tor's work and outlined broader mission, but our focus is on a specific sub-area of theirs:
|
||||
|
||||
> Building tools to help everyone withstand today's mass surveillance.
|
||||
|
||||
We mean *everyone*. We want my mom and your mom to be able to conveniently withstand mass surveillance without having to venture deep into tech. This is our focus. This is what drives us. It's the reason we get out of bed.
|
||||
|
||||
## Maturity
|
||||
|
||||
Tor was released in 2002, while the SPN will launch in June 2020. It goes without saying that Tor is the far maturer project of the two. The SPN is still in its early days.
|
||||
|
||||
## Scope of Protection
|
||||
## The SPN Protects Your Whole Computer
|
||||
|
||||
The Tor browser has great coverage, supporting all major operating systems. It protects the browser habits of its users and is a breeze to set up. When one additionally wants to safeguard the whole computer via the Tor network one has to use the [operating system tails](https://tails.boum.org/install/index.en.html), which is great at what it does, but hard and technical to set up and use.
|
||||
|
||||
This is one key difference to the SPN. With it, it's a simple plug and play. You download the open source app and then it takes care of all your connections, not only those of the browser. When launching in June, we will support Windows, with Linux following shortly after. We are planning on supporting Mac and Mobile in the future too, so everybody can enjoy easy privacy with their preferred operating system.
|
||||
This is one key difference to the SPN. With it, it's a simple plug and play. You download the open source app and then it takes care of all your connections, not only those of the browser. Currently, we support Windows and Linux. We are planning on supporting Mac and Mobile in the future too, so everybody can enjoy easy privacy with their preferred operating system.
|
||||
|
||||
Another detail is that Tor does not transport everything, notably UDP traffic. The SPN will support TCP and UDP (+ variants) from the get go and we will see if we will need and implement anything else.
|
||||
|
||||
## Handling Circuits
|
||||
## Tor Is Maturer
|
||||
|
||||
Tor was released in 2002, while the SPN launched in August 2020. It goes without saying that Tor is the far maturer project of the two. The SPN is still in its early days.
|
||||
|
||||
## The SPN Minimizes Travel through the Open Web
|
||||
|
||||
Both Tor and the SPN provide privacy by decoupling the person (ip-address) from the destination. This prevents your Internet Service Provider and everyone else from logging your Internet activities. When no other identification is provided you even arrive at the destination anonymously, meaning the visited server cannot know who you are.
|
||||
|
||||
|
|
@ -54,9 +39,7 @@ When the connection arrives at the last server of the circuit it still has to tr
|
|||
|
||||
With the SPN however, every connection is calculated individually and leaves the network as near to the destination as possible. This means:
|
||||
|
||||
<br/>
|
||||
|
||||
1. your connections are spread across the globe
|
||||
1. your connections are spread across the globe, creating vast amounts of identities
|
||||
2. visibility in the 'open web' is minimized
|
||||
3. connections are not slowed down by having to go extra miles
|
||||
|
||||
|
|
@ -64,14 +47,14 @@ With the SPN however, every connection is calculated individually and leaves the
|
|||
|
||||
## Minor comments
|
||||
|
||||
**The Dark Web**
|
||||
Tor's mission for anonymity also enables people to host content anonymously through onion domains. This is a non goal for Safing.
|
||||
**The Dark Web Is a Non-Goal for Safing**
|
||||
Tor's mission for anonymity also enables people to host content anonymously through onion domains. This is a non-goal for Safing.
|
||||
|
||||
**SPN enforces DoT**
|
||||
While the open source SPN app sits at the kernel, it can do all sorts of amazing stuff. It will enforce all your DNS queries to use DNS over TLS (DoT), which also prevents your router from snooping on you. Later, it will also block malicious connections via an integrated Application Firewall.
|
||||
**SPN Enforces DoT and Blocks Ads/Trackers**
|
||||
As the [open source Portmaster app]({{ site.github_url }}/portmaster/), which hosts the SPN, sits at the kernel, it can add all sorts of amazing privacy features. Current modules (free & optional) include a DNS Resolver which enforces all your DNS queries to use DNS over TLS (DoT) and a Privacy Filter which blocks malicious or unwanted connections.
|
||||
|
||||
**Free vs Paid product**
|
||||
**The SPN Costs Money**
|
||||
Both the SPN and Tor are FOSS. But Tor is free to use while you have to subscribe to the SPN in order to use it. Be aware you are not only paying for the SPN, but also supporting us to develop the free application firewall and enabling us to continue fighting for a brighter future.
|
||||
|
||||
## Conclusion
|
||||
## Conclusion: It Depends on Your Threat Model
|
||||
Tor is a great project which has pioneered privacy technology and is a firm player in the space while the SPN has fresh, innovative solutions which tackle uncharted ground and focuses on ease of use before all. Depending on your threat model, the SPN may be an alternative to Tor. Or it might not.
|
||||
|
|
|
|||
|
|
@ -1,25 +1,25 @@
|
|||
---
|
||||
title: How the SPN compares to VPNs
|
||||
title: How the SPN Compares to VPNs
|
||||
date: 2020-01-22
|
||||
author: davegson
|
||||
custom_thumbnail_name: how-the-spn-compares-to-vpns
|
||||
cover_image_source: https://pixabay.com/vectors/the-globe-globe-the-internet-free-4790044/
|
||||
---
|
||||
|
||||
## Introduction into VPN Technology
|
||||
## Overview of VPN Technology
|
||||
|
||||
### What is a VPN here for?
|
||||
### VPNs Were Built for Security, NOT for Privacy
|
||||
The VPN technology was developed to allow remote workers to securely connect to a corporate network to virtually check into the office and access internal resources. It does this by establishing a secure tunnel between the worker and the company. The VPN shields the whole route from the worker to the office, never entering the "open Internet".
|
||||
|
||||
### What do commercial VPNs do?
|
||||
Naturally, they do something very similar. As an example, let's say you want to connect to "google.com" via a VPN. The VPN client first creates a safe tunnel to the VPN server, which then calls upon "google.com". So a VPN safeguards your connections up until the VPN server, then unpacks their protection and routes it back into the open Internet.
|
||||
### Commercial VPNs Are just Proxy Servers
|
||||
A commercial VPNs does something rather mundane. As an example, let's say you want to connect to "google.com" via a VPN. The VPN client first creates a safe tunnel to the VPN server, which then calls upon "google.com". So a VPN safeguards your connections up until the VPN server, then unpacks their protection and routes it back into the open Internet.
|
||||
|
||||
### VPNs do not protect your privacy
|
||||
### VPNs do NOT Protect Your Privacy
|
||||
There are many legitimate use cases for a VPN, like securely connecting to your corporate network or "beaming" into another country to enjoy different content or cheaper prices. But VPNs do *not* protect your privacy.
|
||||
|
||||
## Meta Data Collection
|
||||
## The SPN Truly Protects Your Meta Data
|
||||
|
||||
A VPN does protect you from your Internet Service Provider (ISP) to collect and process you browsing activities. But this just delegates the problem: now the VPN that can collect and sell all your data, which many of them do.
|
||||
Before diving into the SPN, let's recap: A VPN does protect you from your Internet Service Provider (ISP) to collect and process you browsing activities. But in the end this just delegates the problem: now the VPN that can collect and sell all your data, which many of them do.
|
||||
|
||||
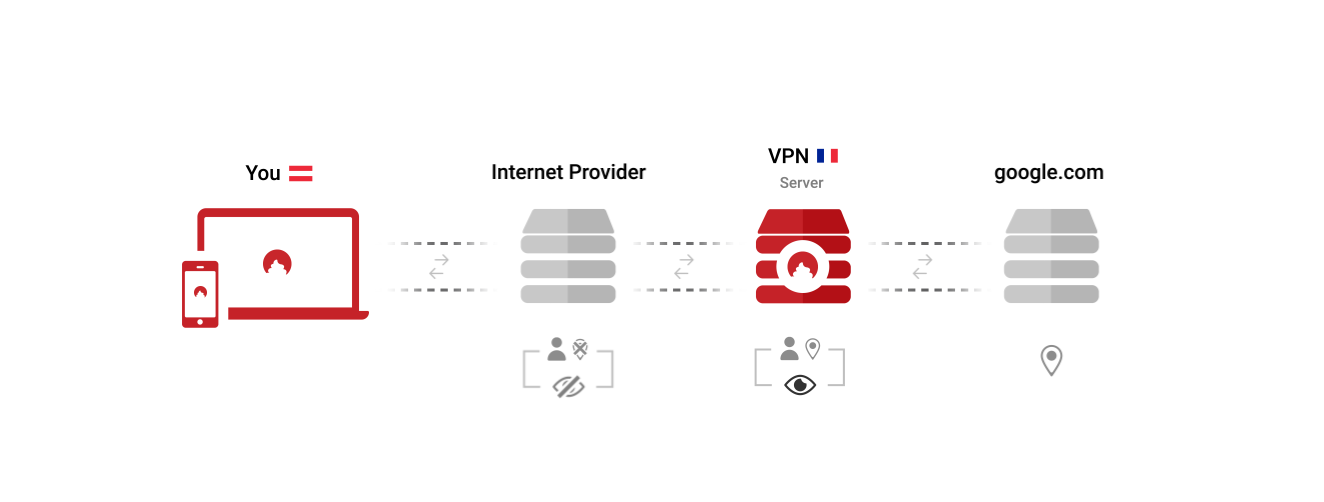
|
||||
|
||||
|
|
@ -29,7 +29,7 @@ The SPN however decouples the person from the destination, resulting in true pri
|
|||
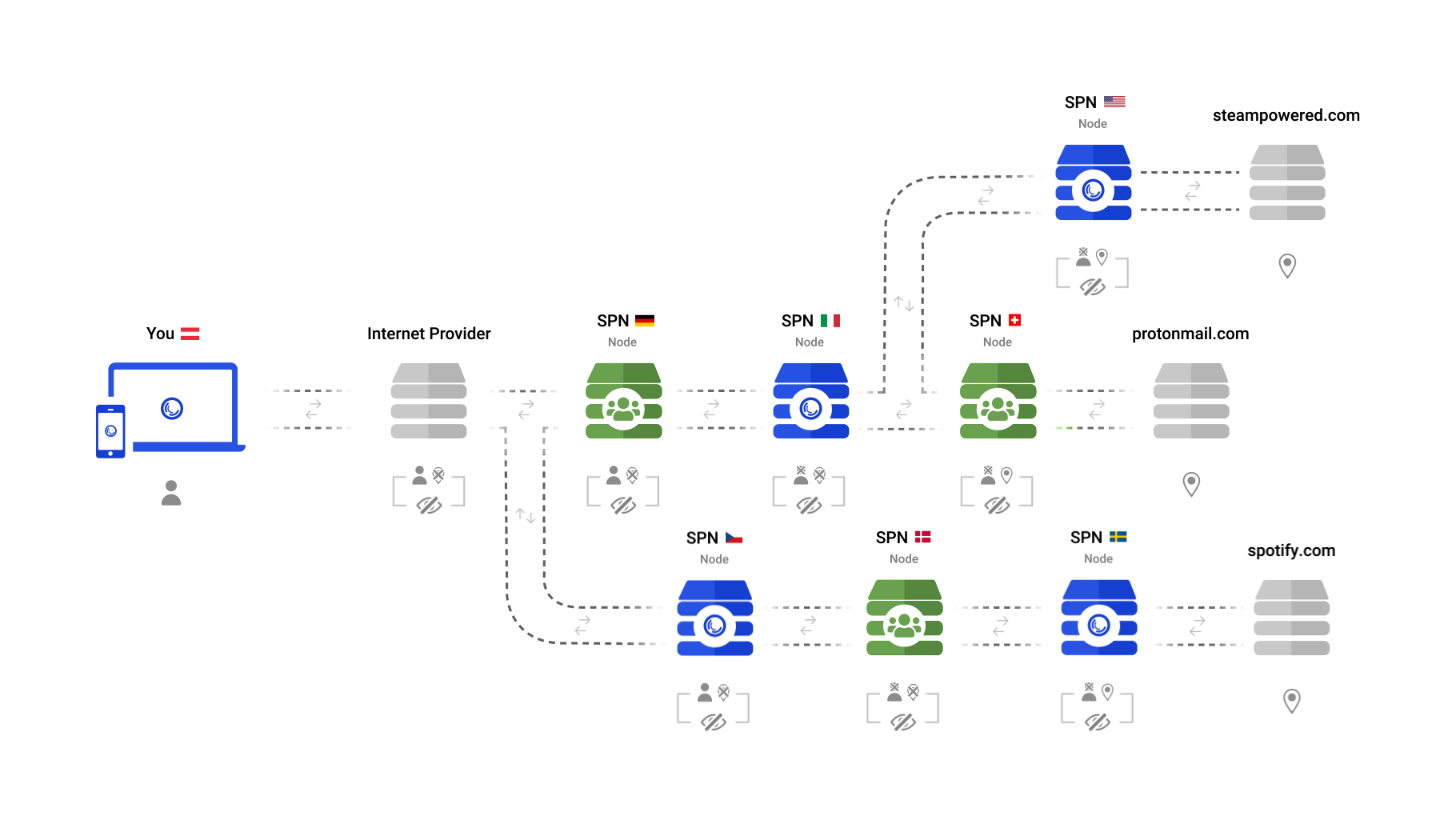
|
||||
|
||||
|
||||
## Scope of Protection
|
||||
## VPN Technology is More Widespread (for now)
|
||||
|
||||
The VPN technology is widespread and almost every computer and mobile phone supports connecting to a VPN natively.
|
||||
|
||||
|
|
@ -37,20 +37,18 @@ When launching in June, the SPN will support Windows, with Linux following short
|
|||
|
||||
The VPN and SPN both tunnel connections from your whole computer, not only from your browser.
|
||||
|
||||
## Open Source
|
||||
## SPN ♥ Open Source - Everybody Can Inspect
|
||||
Many commercial VPN providers use bold and misleading marketing claims without any evidence to back it up. The code on their servers and mostly on their clients cannot be investigated. They demand your trust but give little to no proof in return.
|
||||
|
||||
The SPN however is open source / FOSS. We do not believe users should simply 'trust' companies when it comes to their privacy. Instead they should be able to inspect vendors and hold them accountable publicly. So feel free to check out [our Github](https://github.com/Safing/).
|
||||
The [SPN however is open source / FOSS]({{ site.github_url }}/spn/). We do not believe users should simply 'trust' companies when it comes to their privacy. Instead they should be able to inspect vendors and hold them accountable publicly. Feel free to [check out all of our Github](https://github.com/Safing/).
|
||||
|
||||
## Extra Mileage
|
||||
## The SPN Minimizes Travel through the Open Web
|
||||
|
||||
After a connection arrives at the VPN server it still has to travel to the desired website. Depending on where your VPN is located, this may lead to a slower Internet experience. As an example, a person who is located in Europe may be connected to a US VPN server while loading a European website. This means the connection has to cross the Atlantic twice (EU -> US -> EU).
|
||||
|
||||
With the SPN however, every connection is calculated individually and leaves the network as near to the destination as possible. This means:
|
||||
|
||||
<br/>
|
||||
|
||||
1. your connections are spread across the globe
|
||||
1. your connections are spread across the globe, creating vast amounts of identities
|
||||
2. visibility in the 'open web' is minimized
|
||||
3. connections are not slowed down by having to go extra miles
|
||||
|
||||
|
|
@ -58,15 +56,15 @@ With the SPN however, every connection is calculated individually and leaves the
|
|||
|
||||
## Minor comments
|
||||
|
||||
**SPN enforces DoT**
|
||||
While the open source SPN app sits at the kernel, it can do all sorts of amazing stuff. It will enforce all your DNS queries to use DNS over TLS (DoT), which also prevents your router from snooping on you. Later, it will also block malicious connections via an integrated Application Firewall.
|
||||
**SPN Enforces DoT and Blocks Ads/Trackers**
|
||||
As the [open source Portmaster app]({{ site.github_url }}/portmaster/), which hosts the SPN, sits at the kernel, it can add all sorts of amazing privacy features. Current modules (free & optional) include a DNS Resolver which enforces all your DNS queries to use DNS over TLS (DoT) and a Privacy Filter which blocks malicious or unwanted connections.
|
||||
|
||||
**VPN - a Very Precarious Narrative**
|
||||
There is [a great write up by Dennis Schubert](https://schub.wtf/blog/2019/04/08/very-precarious-narrative.html) showcasing the problem of todays commercial VPNs, both from a privacy and security perspective. Feel free to check it out, it also shows the valid use cases of VPNs.
|
||||
|
||||
**Pricing**
|
||||
**The SPN Costs more Because it is a New Product**
|
||||
While VPN providers basically rebrand the same basic technologies widely available, we built every aspect of the network from the ground up, by hand. This is a huge investment and will require lots of resources to properly maintain and improve. But this is the only way to achieve real privacy. Thank you for enabling us to continue fighting for a brighter future!
|
||||
|
||||
## Conclusion
|
||||
## Conclusion: SPN > VPN
|
||||
|
||||
The VPN technology was built to securely connect two company locations. However, the SPN was developed from the ground up to protect user privacy. As a result the SPN can easily outperform VPNs in every aspect.
|
||||
|
|
|
|||
|
|
@ -14,7 +14,7 @@ This is that story. And the story of shortcuts.
|
|||
|
||||
## Step 1: Creating a Product
|
||||
|
||||
### Grinding it out with R & D
|
||||
### Grind it out with R & D
|
||||
|
||||
There's one question that every company answers before starting out: "What problem are you trying to solve?"
|
||||
|
||||
|
|
@ -22,7 +22,7 @@ Then you go to the drafting board, you research deep into the issue, you think t
|
|||
|
||||
This process is called Research & Development. Nothing novel out there 'just happened', instead, an idea was cultivated and progressed through plenty of trials and errors until it matured into a workable solution.
|
||||
|
||||
### The Shortcut
|
||||
### The Shortcut: Just Copy Work
|
||||
|
||||
But what if you do not have the time for all that? It's rather easy actually, you just copy a current solution. Or you only slightly add functionality to an existing product. The devil's advocate would call this stealing, the marketer would simply describe it as rebranding.
|
||||
|
||||
|
|
@ -34,7 +34,7 @@ With a novel or rebranded product, you're ready to move ahead. But nothing is ga
|
|||
|
||||
## Step 2: Marketing and Growth
|
||||
|
||||
### Putting in the honest work
|
||||
### Listen and Put in Honest Work
|
||||
|
||||
If you have the perfect solution to a problem but nobody knows about it, was the problem really solved? Was your solution really any good? Honestly, no. This is the reason why marketing is *necessary*.
|
||||
|
||||
|
|
@ -44,7 +44,7 @@ But talking to your market has become difficult. In today's information overflow
|
|||
|
||||
For generic growth, there is no way around listening to your audience, being honest and open, and ultimately building a relationship with your customers. Only time, genuine effort and persistence will get you there.
|
||||
|
||||
### The Shortcut
|
||||
### The Shortcut: Just Buy Attention
|
||||
|
||||
Oh yeah, there is a way around this too. Instead of putting in the work, just buy yourself into the game: With todays ad industry, you can simply spend hundreds of thousands of dollars to buy people's attention and hopefully convert enough of them into customers.
|
||||
|
||||
|
|
@ -54,7 +54,7 @@ The catch with this however is that you normally have to turn to venture capital
|
|||
|
||||
Marketing is the act of talking and promoting your product to the market. As a result, growth is *only* possible through good marketing. The ethics behind it all is another story, but I assume you can guess my stance on that topic ;)
|
||||
|
||||
## Convergence
|
||||
## Failing One Step Results in Overall Failure
|
||||
|
||||
Think about different companies and their approach in both these steps. What about those who chose to copy old technology but market it in an honest way? What about those that took the shortcut in both cases? What about the geniuses who researched a break-through solution but failed to present and market it to the world?
|
||||
|
||||
|
|
|
|||
|
|
@ -13,18 +13,14 @@ Future provider changes will always be communicated widely & with a heads-up.
|
|||
|
||||
Changes of _their order_ will happen from time to time and only be communicated in our Github update logs. We need this flexibility to adapt to ever-changing environments, both in organizational and technical terms.
|
||||
|
||||
<br/>
|
||||
|
||||
---
|
||||
|
||||
<br/>
|
||||
|
||||
### How the Portmaster Uses DNS Servers
|
||||
|
||||
At release of this post the default DNS providers is set to:
|
||||
|
||||
- 1. Quad9
|
||||
- 2. Cloudflare
|
||||
1. Quad9
|
||||
2. Cloudflare
|
||||
|
||||
This means the primary resolver is Quad9 (1). Only when issues arise with Quad9, will the Portmaster fall back to Cloudflare (2). The same applies when a third, fourth, etc., provider is configured.
|
||||
|
||||
|
|
|
|||
150
_sass/_blog.scss
Normal file
150
_sass/_blog.scss
Normal file
|
|
@ -0,0 +1,150 @@
|
|||
#page-container content #blog {
|
||||
padding-top: 3rem;
|
||||
|
||||
hr{
|
||||
margin-top: 2rem;
|
||||
margin-bottom: 2rem;
|
||||
}
|
||||
|
||||
p {
|
||||
padding-top: 1.4rem;
|
||||
color: #898989;
|
||||
}
|
||||
|
||||
strong {
|
||||
color: black;
|
||||
}
|
||||
|
||||
a:hover {
|
||||
opacity: .5;
|
||||
transition-duration: 150ms;
|
||||
transition-timing-function: cubic-bezier(.4, 0, .2, 1);
|
||||
}
|
||||
|
||||
a {
|
||||
--text-opacity: 1;
|
||||
color: #667eea;
|
||||
color: rgba(102, 126, 234, var(--text-opacity));
|
||||
text-decoration: inherit;
|
||||
background-color: transparent;
|
||||
transition-property: background-color, border-color, color, fill, stroke, opacity, box-shadow, transform;
|
||||
}
|
||||
|
||||
a strong {
|
||||
--text-opacity: 1;
|
||||
color: #667eea;
|
||||
color: rgba(102, 126, 234, var(--text-opacity));
|
||||
}
|
||||
|
||||
h2 {
|
||||
font-size: 1.875rem;
|
||||
padding-top: 3.5rem;
|
||||
font-weight: 800;
|
||||
}
|
||||
|
||||
h3 {
|
||||
font-size: 1.2rem;
|
||||
padding-top: 1rem;
|
||||
font-weight: 800;
|
||||
}
|
||||
|
||||
h4 {
|
||||
font-size: 1.1rem;
|
||||
padding-top: 1rem;
|
||||
font-weight: 500;
|
||||
}
|
||||
|
||||
ul, ol {
|
||||
padding-top: 1rem;
|
||||
padding-bottom: 1rem;
|
||||
}
|
||||
|
||||
ul li {
|
||||
padding-top: 0.4rem;
|
||||
}
|
||||
|
||||
ol li {
|
||||
padding-top: 0.4rem;
|
||||
}
|
||||
|
||||
blockquote {
|
||||
border-left: 2px solid #ccc;
|
||||
margin: 1rem 10px;
|
||||
padding: 0.5em 25px;
|
||||
}
|
||||
blockquote:before {
|
||||
color: #ccc;
|
||||
font-size: 4em;
|
||||
line-height: 0.1em;
|
||||
margin-right: 0.25em;
|
||||
vertical-align: -0.4em;
|
||||
}
|
||||
blockquote p {
|
||||
display: inline;
|
||||
font-weight: 500;
|
||||
font-style: italic;
|
||||
padding-left: 0;
|
||||
color: black;
|
||||
}
|
||||
|
||||
.content {
|
||||
max-width: 750px;
|
||||
margin: auto;
|
||||
margin-top: 3rem;
|
||||
|
||||
ul {
|
||||
padding-top: 0.1rem;
|
||||
list-style-type: initial;
|
||||
padding-left: 1rem;
|
||||
color: #898989;
|
||||
}
|
||||
|
||||
ol {
|
||||
padding-top: 0.1rem;
|
||||
list-style-type: decimal;
|
||||
padding-left: 1rem;
|
||||
color: #898989;
|
||||
}
|
||||
|
||||
blockquote p {
|
||||
font-weight: bold;
|
||||
padding-left: 2rem;
|
||||
color: black;
|
||||
opacity: 0.6;
|
||||
}
|
||||
|
||||
p {
|
||||
padding: 0.5rem 0;
|
||||
}
|
||||
|
||||
p img {
|
||||
--transform-translate-x: 0;
|
||||
--transform-translate-y: 0;
|
||||
--transform-rotate: 0;
|
||||
--transform-skew-x: 0;
|
||||
--transform-skew-y: 0;
|
||||
--transform-scale-x: 1.1;
|
||||
--transform-scale-y: 1.1;
|
||||
transform: translateX(var(--transform-translate-x)) translateY(var(--transform-translate-y)) rotate(var(--transform-rotate)) skewX(var(--transform-skew-x)) skewY(var(--transform-skew-y)) scaleX(var(--transform-scale-x)) scaleY(var(--transform-scale-y));
|
||||
box-shadow: 0 0px 90px 0 rgba(59, 93, 199, 0.1), 0 0px 5px 0 rgba(0, 0, 0, 0);
|
||||
margin-top: 5rem;
|
||||
max-width: 100%;
|
||||
height: auto;
|
||||
border-radius: .375rem;
|
||||
display: block;
|
||||
margin-bottom: 4rem;
|
||||
margin-top: 5rem;
|
||||
}
|
||||
|
||||
.podcast h2 {
|
||||
padding-top: 1rem;
|
||||
font-weight: 500;
|
||||
font-size: 1rem;
|
||||
padding-bottom: 0.5rem;
|
||||
}
|
||||
|
||||
audio {
|
||||
padding-bottom: 1.5rem;
|
||||
}
|
||||
}
|
||||
}
|
||||
|
|
@ -2,6 +2,10 @@
|
|||
font-family: "Roboto";
|
||||
}
|
||||
|
||||
a{
|
||||
word-break: break-all;
|
||||
}
|
||||
|
||||
body {
|
||||
overflow-x: hidden;
|
||||
}
|
||||
|
|
@ -211,7 +215,7 @@ a.link {
|
|||
}
|
||||
|
||||
|
||||
.shadowthing{
|
||||
.cardshadow{
|
||||
box-shadow: 0 0px 5px 0 rgba(0, 0, 0, 0), 0 0px 90px 0 rgba(59, 93, 199, 0.1);
|
||||
}
|
||||
|
||||
|
|
@ -219,7 +223,7 @@ a.link {
|
|||
display: grid;
|
||||
grid-template-columns: repeat(1, auto);
|
||||
grid-template-rows: auto;
|
||||
grid-row-gap: 3px;
|
||||
grid-row-gap: 15px;
|
||||
grid-auto-flow: row;
|
||||
margin-left: auto;
|
||||
margin-right: auto;
|
||||
|
|
|
|||
|
|
@ -3,3 +3,4 @@
|
|||
|
||||
@import "global";
|
||||
@import "page_container";
|
||||
@import "blog";
|
||||
|
|
@ -41,7 +41,7 @@ layout: page
|
|||
{% if site.data.next.cards.in_progress.size > 0 %}
|
||||
<div class="pt-64">
|
||||
<div class="nextwrapper">
|
||||
<div style="margin-top: -8rem;" class="absolute pl-8 ">
|
||||
<div class="absolute pl-8 -mt-48 sm:-mt-32">
|
||||
<div >
|
||||
<span class="opacity-50">In Progress</span>
|
||||
<strong class="pl-2 opacity-75">({{ site.data.next.cards.in_progress.size }})</strong>
|
||||
|
|
|
|||
|
|
@ -509,16 +509,6 @@ acceptance of our Privacy Policy, we recommend that subscribers check
|
|||
for updates and reads said content of any amended policies we might make
|
||||
in the future.
|
||||
|
||||
**Amendment 0.1. 05/08/2020**
|
||||
|
||||
Due to the Court of Justice of the European Union ruling on data transfers,
|
||||
invalidating the Privacy Shield and GDPR compliance of such a ruling.
|
||||
It is here by stated that Safing ICS Technologies GmbH, does not hold or
|
||||
transfer any data to any servers held in the United States of America,
|
||||
however, due to the operating nature of the SPN, we cannot and will not
|
||||
be held responsible for any private nodes held within the United States
|
||||
of America that you choose to use.
|
||||
|
||||
## Article 19. Contact
|
||||
|
||||
If you have any questions regarding our Privacy Policy and how we handle
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue