- -1. your connections are spread across the globe +1. your connections are spread across the globe, creating vast amounts of identities 2. visibility in the 'open web' is minimized 3. connections are not slowed down by having to go extra miles @@ -64,14 +47,14 @@ With the SPN however, every connection is calculated individually and leaves the ## Minor comments -**The Dark Web** -Tor's mission for anonymity also enables people to host content anonymously through onion domains. This is a non goal for Safing. +**The Dark Web Is a Non-Goal for Safing** +Tor's mission for anonymity also enables people to host content anonymously through onion domains. This is a non-goal for Safing. -**SPN enforces DoT** -While the open source SPN app sits at the kernel, it can do all sorts of amazing stuff. It will enforce all your DNS queries to use DNS over TLS (DoT), which also prevents your router from snooping on you. Later, it will also block malicious connections via an integrated Application Firewall. +**SPN Enforces DoT and Blocks Ads/Trackers** +As the [open source Portmaster app]({{ site.github_url }}/portmaster/), which hosts the SPN, sits at the kernel, it can add all sorts of amazing privacy features. Current modules (free & optional) include a DNS Resolver which enforces all your DNS queries to use DNS over TLS (DoT) and a Privacy Filter which blocks malicious or unwanted connections. -**Free vs Paid product** +**The SPN Costs Money** Both the SPN and Tor are FOSS. But Tor is free to use while you have to subscribe to the SPN in order to use it. Be aware you are not only paying for the SPN, but also supporting us to develop the free application firewall and enabling us to continue fighting for a brighter future. -## Conclusion +## Conclusion: It Depends on Your Threat Model Tor is a great project which has pioneered privacy technology and is a firm player in the space while the SPN has fresh, innovative solutions which tackle uncharted ground and focuses on ease of use before all. Depending on your threat model, the SPN may be an alternative to Tor. Or it might not. diff --git a/_posts/2020-01-22-how-the-spn-compares-to-vpns.md b/_posts/2020-01-22-how-the-spn-compares-to-vpns.md index 3cc4331..08470df 100644 --- a/_posts/2020-01-22-how-the-spn-compares-to-vpns.md +++ b/_posts/2020-01-22-how-the-spn-compares-to-vpns.md @@ -1,25 +1,25 @@ --- -title: How the SPN compares to VPNs +title: How the SPN Compares to VPNs date: 2020-01-22 author: davegson custom_thumbnail_name: how-the-spn-compares-to-vpns cover_image_source: https://pixabay.com/vectors/the-globe-globe-the-internet-free-4790044/ --- -## Introduction into VPN Technology +## Overview of VPN Technology -### What is a VPN here for? +### VPNs Were Built for Security, NOT for Privacy The VPN technology was developed to allow remote workers to securely connect to a corporate network to virtually check into the office and access internal resources. It does this by establishing a secure tunnel between the worker and the company. The VPN shields the whole route from the worker to the office, never entering the "open Internet". -### What do commercial VPNs do? -Naturally, they do something very similar. As an example, let's say you want to connect to "google.com" via a VPN. The VPN client first creates a safe tunnel to the VPN server, which then calls upon "google.com". So a VPN safeguards your connections up until the VPN server, then unpacks their protection and routes it back into the open Internet. +### Commercial VPNs Are just Proxy Servers +A commercial VPNs does something rather mundane. As an example, let's say you want to connect to "google.com" via a VPN. The VPN client first creates a safe tunnel to the VPN server, which then calls upon "google.com". So a VPN safeguards your connections up until the VPN server, then unpacks their protection and routes it back into the open Internet. -### VPNs do not protect your privacy +### VPNs do NOT Protect Your Privacy There are many legitimate use cases for a VPN, like securely connecting to your corporate network or "beaming" into another country to enjoy different content or cheaper prices. But VPNs do *not* protect your privacy. -## Meta Data Collection +## The SPN Truly Protects Your Meta Data -A VPN does protect you from your Internet Service Provider (ISP) to collect and process you browsing activities. But this just delegates the problem: now the VPN that can collect and sell all your data, which many of them do. +Before diving into the SPN, let's recap: A VPN does protect you from your Internet Service Provider (ISP) to collect and process you browsing activities. But in the end this just delegates the problem: now the VPN that can collect and sell all your data, which many of them do. 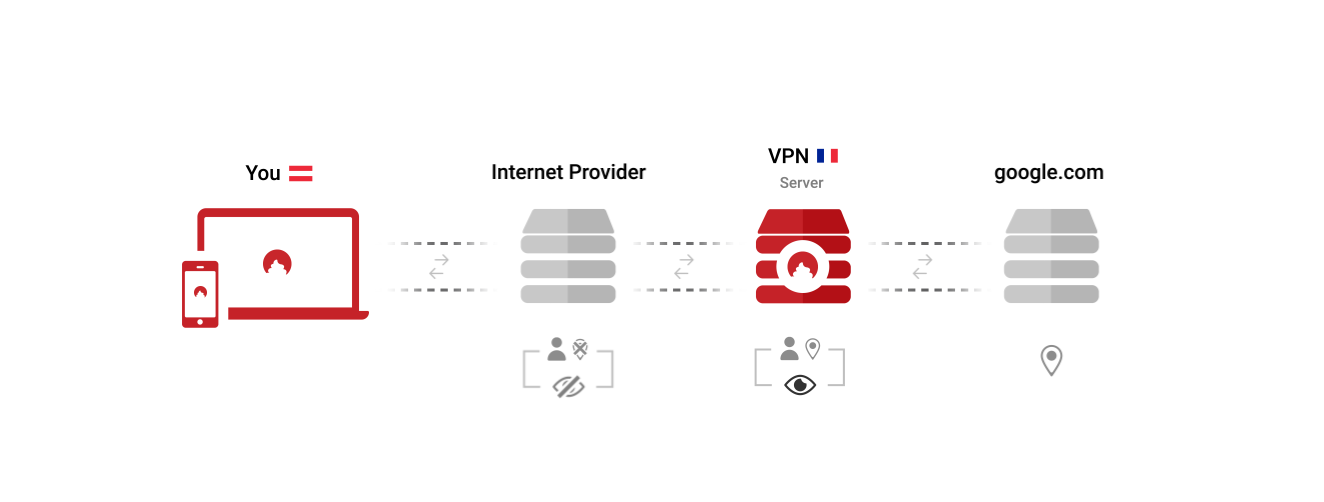 @@ -29,7 +29,7 @@ The SPN however decouples the person from the destination, resulting in true pri 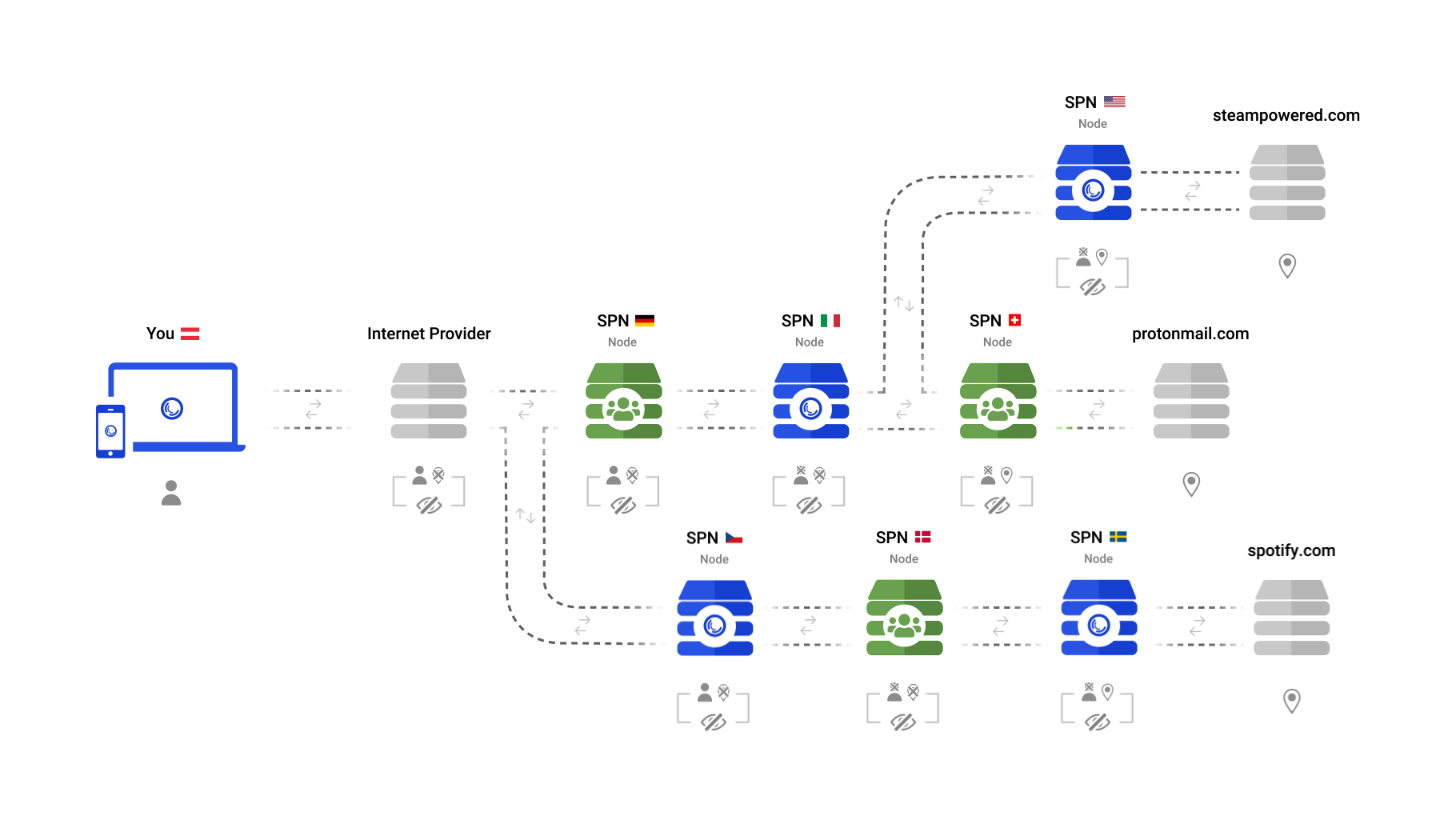 -## Scope of Protection +## VPN Technology is More Widespread (for now) The VPN technology is widespread and almost every computer and mobile phone supports connecting to a VPN natively. @@ -37,20 +37,18 @@ When launching in June, the SPN will support Windows, with Linux following short The VPN and SPN both tunnel connections from your whole computer, not only from your browser. -## Open Source +## SPN ♥ Open Source - Everybody Can Inspect Many commercial VPN providers use bold and misleading marketing claims without any evidence to back it up. The code on their servers and mostly on their clients cannot be investigated. They demand your trust but give little to no proof in return. -The SPN however is open source / FOSS. We do not believe users should simply 'trust' companies when it comes to their privacy. Instead they should be able to inspect vendors and hold them accountable publicly. So feel free to check out [our Github](https://github.com/Safing/). +The [SPN however is open source / FOSS]({{ site.github_url }}/spn/). We do not believe users should simply 'trust' companies when it comes to their privacy. Instead they should be able to inspect vendors and hold them accountable publicly. Feel free to [check out all of our Github](https://github.com/Safing/). -## Extra Mileage +## The SPN Minimizes Travel through the Open Web After a connection arrives at the VPN server it still has to travel to the desired website. Depending on where your VPN is located, this may lead to a slower Internet experience. As an example, a person who is located in Europe may be connected to a US VPN server while loading a European website. This means the connection has to cross the Atlantic twice (EU -> US -> EU). With the SPN however, every connection is calculated individually and leaves the network as near to the destination as possible. This means: -
- -1. your connections are spread across the globe +1. your connections are spread across the globe, creating vast amounts of identities 2. visibility in the 'open web' is minimized 3. connections are not slowed down by having to go extra miles @@ -58,15 +56,15 @@ With the SPN however, every connection is calculated individually and leaves the ## Minor comments -**SPN enforces DoT** -While the open source SPN app sits at the kernel, it can do all sorts of amazing stuff. It will enforce all your DNS queries to use DNS over TLS (DoT), which also prevents your router from snooping on you. Later, it will also block malicious connections via an integrated Application Firewall. +**SPN Enforces DoT and Blocks Ads/Trackers** +As the [open source Portmaster app]({{ site.github_url }}/portmaster/), which hosts the SPN, sits at the kernel, it can add all sorts of amazing privacy features. Current modules (free & optional) include a DNS Resolver which enforces all your DNS queries to use DNS over TLS (DoT) and a Privacy Filter which blocks malicious or unwanted connections. **VPN - a Very Precarious Narrative** There is [a great write up by Dennis Schubert](https://schub.wtf/blog/2019/04/08/very-precarious-narrative.html) showcasing the problem of todays commercial VPNs, both from a privacy and security perspective. Feel free to check it out, it also shows the valid use cases of VPNs. -**Pricing** +**The SPN Costs more Because it is a New Product** While VPN providers basically rebrand the same basic technologies widely available, we built every aspect of the network from the ground up, by hand. This is a huge investment and will require lots of resources to properly maintain and improve. But this is the only way to achieve real privacy. Thank you for enabling us to continue fighting for a brighter future! -## Conclusion +## Conclusion: SPN > VPN The VPN technology was built to securely connect two company locations. However, the SPN was developed from the ground up to protect user privacy. As a result the SPN can easily outperform VPNs in every aspect. diff --git a/_posts/2020-02-04-the-two-steps-it-takes.md b/_posts/2020-02-04-the-two-steps-it-takes.md index 3e3ba95..24b2221 100644 --- a/_posts/2020-02-04-the-two-steps-it-takes.md +++ b/_posts/2020-02-04-the-two-steps-it-takes.md @@ -14,7 +14,7 @@ This is that story. And the story of shortcuts. ## Step 1: Creating a Product -### Grinding it out with R & D +### Grind it out with R & D There's one question that every company answers before starting out: "What problem are you trying to solve?" @@ -22,7 +22,7 @@ Then you go to the drafting board, you research deep into the issue, you think t This process is called Research & Development. Nothing novel out there 'just happened', instead, an idea was cultivated and progressed through plenty of trials and errors until it matured into a workable solution. -### The Shortcut +### The Shortcut: Just Copy Work But what if you do not have the time for all that? It's rather easy actually, you just copy a current solution. Or you only slightly add functionality to an existing product. The devil's advocate would call this stealing, the marketer would simply describe it as rebranding. @@ -34,7 +34,7 @@ With a novel or rebranded product, you're ready to move ahead. But nothing is ga ## Step 2: Marketing and Growth -### Putting in the honest work +### Listen and Put in Honest Work If you have the perfect solution to a problem but nobody knows about it, was the problem really solved? Was your solution really any good? Honestly, no. This is the reason why marketing is *necessary*. @@ -44,7 +44,7 @@ But talking to your market has become difficult. In today's information overflow For generic growth, there is no way around listening to your audience, being honest and open, and ultimately building a relationship with your customers. Only time, genuine effort and persistence will get you there. -### The Shortcut +### The Shortcut: Just Buy Attention Oh yeah, there is a way around this too. Instead of putting in the work, just buy yourself into the game: With todays ad industry, you can simply spend hundreds of thousands of dollars to buy people's attention and hopefully convert enough of them into customers. @@ -54,7 +54,7 @@ The catch with this however is that you normally have to turn to venture capital Marketing is the act of talking and promoting your product to the market. As a result, growth is *only* possible through good marketing. The ethics behind it all is another story, but I assume you can guess my stance on that topic ;) -## Convergence +## Failing One Step Results in Overall Failure Think about different companies and their approach in both these steps. What about those who chose to copy old technology but market it in an honest way? What about those that took the shortcut in both cases? What about the geniuses who researched a break-through solution but failed to present and market it to the world? diff --git a/_posts/2020-07-07-we-are-updating-portmasters-default-dns-servers.md b/_posts/2020-07-07-we-are-updating-portmasters-default-dns-servers.md index b0bf5e4..aa90eee 100644 --- a/_posts/2020-07-07-we-are-updating-portmasters-default-dns-servers.md +++ b/_posts/2020-07-07-we-are-updating-portmasters-default-dns-servers.md @@ -13,18 +13,14 @@ Future provider changes will always be communicated widely & with a heads-up. Changes of _their order_ will happen from time to time and only be communicated in our Github update logs. We need this flexibility to adapt to ever-changing environments, both in organizational and technical terms. -
- --- -
- ### How the Portmaster Uses DNS Servers At release of this post the default DNS providers is set to: -- 1. Quad9 -- 2. Cloudflare +1. Quad9 +2. Cloudflare This means the primary resolver is Quad9 (1). Only when issues arise with Quad9, will the Portmaster fall back to Cloudflare (2). The same applies when a third, fourth, etc., provider is configured. diff --git a/_sass/_blog.scss b/_sass/_blog.scss new file mode 100644 index 0000000..3641553 --- /dev/null +++ b/_sass/_blog.scss @@ -0,0 +1,150 @@ +#page-container content #blog { + padding-top: 3rem; + + hr{ + margin-top: 2rem; + margin-bottom: 2rem; + } + + p { + padding-top: 1.4rem; + color: #898989; + } + + strong { + color: black; + } + + a:hover { + opacity: .5; + transition-duration: 150ms; + transition-timing-function: cubic-bezier(.4, 0, .2, 1); + } + + a { + --text-opacity: 1; + color: #667eea; + color: rgba(102, 126, 234, var(--text-opacity)); + text-decoration: inherit; + background-color: transparent; + transition-property: background-color, border-color, color, fill, stroke, opacity, box-shadow, transform; + } + + a strong { + --text-opacity: 1; + color: #667eea; + color: rgba(102, 126, 234, var(--text-opacity)); + } + + h2 { + font-size: 1.875rem; + padding-top: 3.5rem; + font-weight: 800; + } + + h3 { + font-size: 1.2rem; + padding-top: 1rem; + font-weight: 800; + } + + h4 { + font-size: 1.1rem; + padding-top: 1rem; + font-weight: 500; + } + + ul, ol { + padding-top: 1rem; + padding-bottom: 1rem; + } + + ul li { + padding-top: 0.4rem; + } + + ol li { + padding-top: 0.4rem; + } + + blockquote { + border-left: 2px solid #ccc; + margin: 1rem 10px; + padding: 0.5em 25px; + } + blockquote:before { + color: #ccc; + font-size: 4em; + line-height: 0.1em; + margin-right: 0.25em; + vertical-align: -0.4em; + } + blockquote p { + display: inline; + font-weight: 500; + font-style: italic; + padding-left: 0; + color: black; + } + + .content { + max-width: 750px; + margin: auto; + margin-top: 3rem; + + ul { + padding-top: 0.1rem; + list-style-type: initial; + padding-left: 1rem; + color: #898989; + } + + ol { + padding-top: 0.1rem; + list-style-type: decimal; + padding-left: 1rem; + color: #898989; + } + + blockquote p { + font-weight: bold; + padding-left: 2rem; + color: black; + opacity: 0.6; + } + + p { + padding: 0.5rem 0; + } + + p img { + --transform-translate-x: 0; + --transform-translate-y: 0; + --transform-rotate: 0; + --transform-skew-x: 0; + --transform-skew-y: 0; + --transform-scale-x: 1.1; + --transform-scale-y: 1.1; + transform: translateX(var(--transform-translate-x)) translateY(var(--transform-translate-y)) rotate(var(--transform-rotate)) skewX(var(--transform-skew-x)) skewY(var(--transform-skew-y)) scaleX(var(--transform-scale-x)) scaleY(var(--transform-scale-y)); + box-shadow: 0 0px 90px 0 rgba(59, 93, 199, 0.1), 0 0px 5px 0 rgba(0, 0, 0, 0); + margin-top: 5rem; + max-width: 100%; + height: auto; + border-radius: .375rem; + display: block; + margin-bottom: 4rem; + margin-top: 5rem; + } + + .podcast h2 { + padding-top: 1rem; + font-weight: 500; + font-size: 1rem; + padding-bottom: 0.5rem; + } + + audio { + padding-bottom: 1.5rem; + } + } +} diff --git a/_sass/_global.scss b/_sass/_global.scss index d04f3d2..99e4a45 100644 --- a/_sass/_global.scss +++ b/_sass/_global.scss @@ -2,6 +2,10 @@ font-family: "Roboto"; } +a{ + word-break: break-all; +} + body { overflow-x: hidden; } @@ -211,7 +215,7 @@ a.link { } -.shadowthing{ +.cardshadow{ box-shadow: 0 0px 5px 0 rgba(0, 0, 0, 0), 0 0px 90px 0 rgba(59, 93, 199, 0.1); } @@ -219,7 +223,7 @@ a.link { display: grid; grid-template-columns: repeat(1, auto); grid-template-rows: auto; - grid-row-gap: 3px; + grid-row-gap: 15px; grid-auto-flow: row; margin-left: auto; margin-right: auto; diff --git a/assets/css/main.scss b/assets/css/main.scss index 6035148..25fdebb 100644 --- a/assets/css/main.scss +++ b/assets/css/main.scss @@ -3,3 +3,4 @@ @import "global"; @import "page_container"; +@import "blog"; \ No newline at end of file diff --git a/next/index.html b/next/index.html index 33a2311..9a59a9c 100644 --- a/next/index.html +++ b/next/index.html @@ -41,7 +41,7 @@ layout: page {% if site.data.next.cards.in_progress.size > 0 %}
-
+
In Progress
({{ site.data.next.cards.in_progress.size }})
diff --git a/privacy/index.md b/privacy/index.md
index 84e5276..24a12a0 100644
--- a/privacy/index.md
+++ b/privacy/index.md
@@ -509,16 +509,6 @@ acceptance of our Privacy Policy, we recommend that subscribers check
for updates and reads said content of any amended policies we might make
in the future.
-**Amendment 0.1. 05/08/2020**
-
-Due to the Court of Justice of the European Union ruling on data transfers,
-invalidating the Privacy Shield and GDPR compliance of such a ruling.
-It is here by stated that Safing ICS Technologies GmbH, does not hold or
-transfer any data to any servers held in the United States of America,
-however, due to the operating nature of the SPN, we cannot and will not
-be held responsible for any private nodes held within the United States
-of America that you choose to use.
-
## Article 19. Contact
If you have any questions regarding our Privacy Policy and how we handle