mirror of
https://github.com/safing/web
synced 2025-09-01 02:29:02 +00:00
Remix headers and master some sentences
- make SPN vs VPN flow better - make it readable (at least part 1) by only reading the titles
This commit is contained in:
parent
c359e6777b
commit
072f54b385
1 changed files with 24 additions and 28 deletions
|
|
@ -50,9 +50,11 @@ So only you can decide which solution is best for you.
|
|||
Understanding your threat model might be difficult at first, but it will save you a lot of time and help you avoiding wrong decisions.
|
||||
This comparison blog showcases the strengths and weaknesses of the Portmaster and Simplewall and hopes to assist you in your decision making.
|
||||
|
||||
With this mindest, let's dig into the details.
|
||||
With that mindset, we believe SPN is for people who want more than a simple VPN and at the same time do not have the time or skills to go through the hassle of setting up Tor for their full device.
|
||||
|
||||
### Multiple Identities
|
||||
Now, let us jump into the comparison of SPN vs VPN.
|
||||
|
||||
### A VPN Only Gives You One Identity
|
||||
|
||||
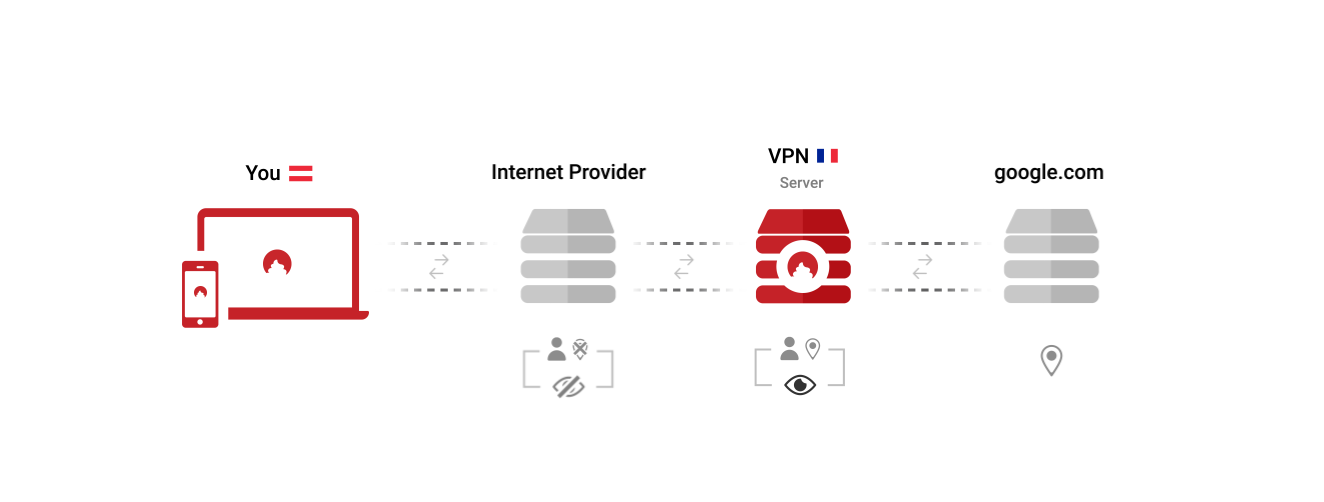
Open any VPN app, and you are presented with your most important choice: Choose the country you want to browse the Internet from. You exchange the identity of being a customer of your ISP with the identity of being a customer of your VPN provider. This is good if you trust your VPN more than your ISP, but it will not fool many trackers.
|
||||
|
||||
|
|
@ -60,8 +62,10 @@ This is how this looks like:
|
|||
|
||||
|
||||
|
||||
When you first open the SPN, it won't ask you from which country you want to browse the Internet. Why limit yourself to one?
|
||||
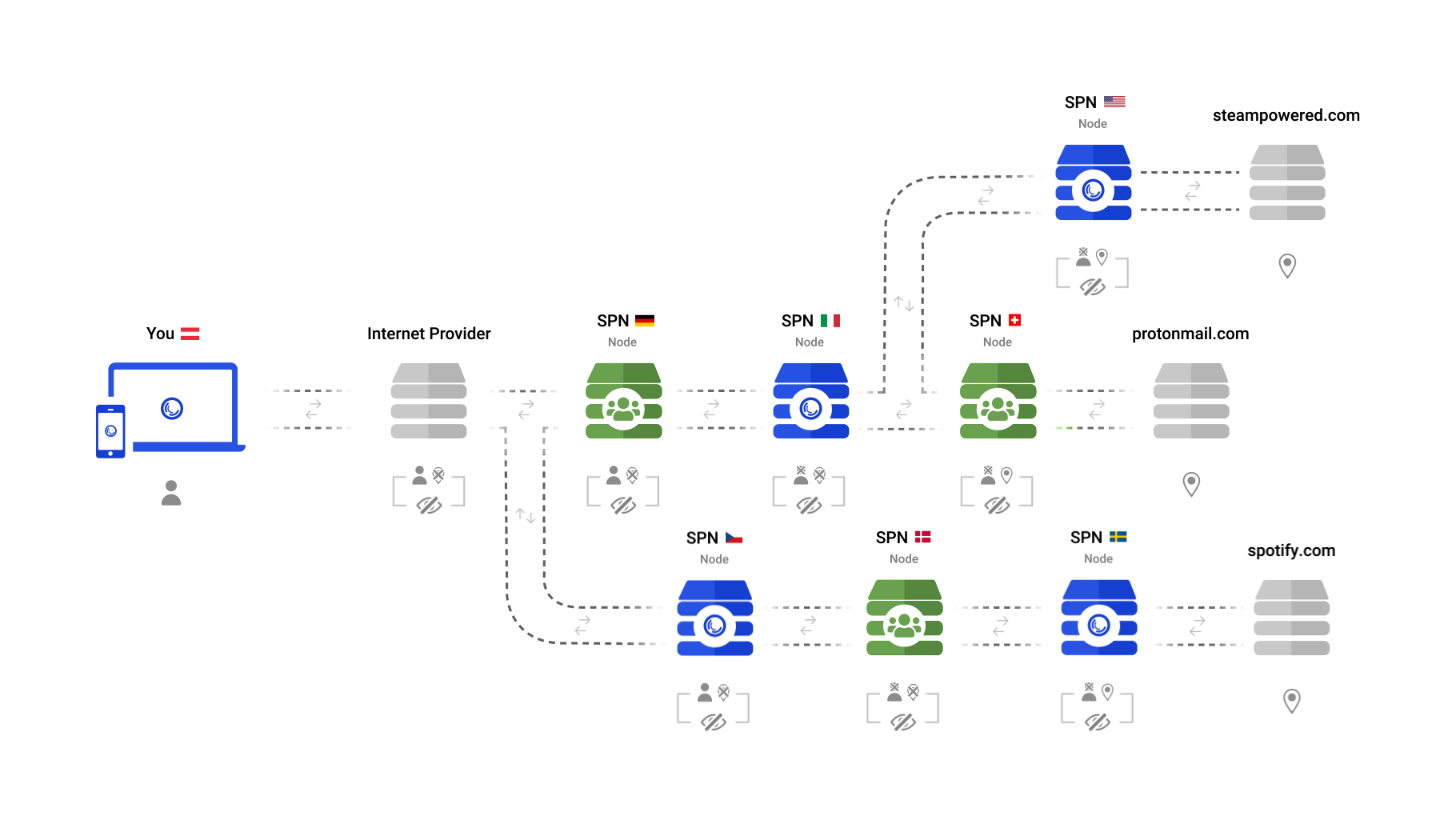
The SPN does not just use one server in one country, but uses many servers in many countries - at the same time. This results in having many identities, not just one.
|
||||
### SPN Gives You Multiple Identities, For Each App
|
||||
|
||||
When you first open the SPN, it will not ask you from which country you want to browse the Internet. Why limit yourself to one?
|
||||
The SPN does not just use one server in one country, but uses many servers in many countries - all at the same time. This results in having many identities, not just one.
|
||||
|
||||
This is how this looks like:
|
||||
|
||||
|
|
@ -71,23 +75,23 @@ Instead of just "beaming" yourself to another place, you can now be everywhere a
|
|||
|
||||
### Automatic Geo-Unblocking
|
||||
|
||||
The longer your connections stay within the SPN, the more private they are. This is why the SPN selects the final server as close as possible to the destination server that you are trying to connect to in order to open a website.
|
||||
The longer your connections stay within the SPN, the more private they are. This is why the SPN selects the final server (exit node) as close as possible to the destination server (eg: server of a website).
|
||||
|
||||
This does not only provide vastly improved privacy, but automatically unblocks geo-restricted content, as you will be accessing the content in the country it originates from.
|
||||
|
||||
In case you have special requirements, you can of course instruct the SPN to use a specific country for a website. _This feature is still in progress._
|
||||
In case you have special requirements, you can of course instruct the SPN to use a specific country for a website. _Note: currently this feature is tricky to set up - it will improve in the future_
|
||||
|
||||
Needless to say, VPNs cannot do this automatically, as they can only use one "exit" server at once, even if they are "multi-hop".
|
||||
|
||||
### Individual App Settings
|
||||
### You Can Easily Exclude Apps or Domains from SPN
|
||||
|
||||
While there are some VPNs that are able to exclude the local network (LAN) or certain apps from the VPN, the SPN takes this to a new level.
|
||||
|
||||
Similar to firewall rules, you can very easily exclude any combination of connections from being routed through the SPN. By default, it excludes local network resources, as well as any captive portal. You do not need to turn it off to log into the WiFi when traveling!
|
||||
Similar to Portmaster firewall rules, you can very easily exclude any combination of domains or apps from being routed through the SPN. By default, it excludes local network resources, as well as any captive portal. You do not need to turn it off to log into the WiFi when traveling!
|
||||
|
||||
### Easy Setup
|
||||
### Both VPNs and SPN Are Easy to Setup
|
||||
|
||||
The SPN is part of Portmaster, which seamlessly integrates into your system and is installed with a single click.
|
||||
SPN is part of Portmaster, which seamlessly integrates into your system and has a super simple installation process.
|
||||
|
||||
Most VPNs provide a custom app that is easy to install - some require you to manually configure a client, though.
|
||||
|
||||
|
|
@ -103,7 +107,7 @@ The SPN is fully open source. Everyone can inspect the code and make sure it doe
|
|||
|
||||
VPNs use a technology first created over 20 years ago with the intent to securely connect two distant private networks. It was never meant to protect a single device from the network, but to enable even more connectivity through a separate channel. The term "Private" in "Virtual Private Network" does not stand for "private as in secret", but for "private as in property".
|
||||
|
||||
Only later companies started to offer a "VPN" as an online privacy solution for individual users. In order to do that, they had to "twist" the VPN technology into a direction it was not created for: protecting a device from the network itself. This is why VPN providers have problems with IP leaks and DNS leaks and try to circumvent the negative side effects with "Kill Switches" and "No Log Policies".
|
||||
Only later companies started to offer a "VPN" as an online privacy solution for individual users. In order to do that, they had to twist the VPN technology into a direction it was not created for: protecting a device from the network itself. This is why VPN providers have problems with IP leaks and DNS leaks and try to circumvent the negative side effects with "Kill Switches" and "No Log Policies".
|
||||
|
||||
<p class="emphasize">
|
||||
The SPN technology, on the other hand, was created from scratch with a single purpose in mind: Protecting your privacy on the Internet. Every single part of the SPN is geared towards this goal. There are no dirty fixes or bandages. Everything is carefully engineered to protect you.
|
||||
|
|
@ -117,19 +121,13 @@ The SPN does not need a kill switch and it does not need "No Log Policies", beca
|
|||
|
||||
The SPN does one thing and it is very good at it: Protecting your privacy.
|
||||
|
||||
### Conclusion: SPN is a better fit for most threat models
|
||||
### Conclusion: SPN Is the Superior Privacy Solution
|
||||
|
||||
Going back to the threat modeling we started with, we believe that many VPN users actually want a level of privacy that VPNs simply cannot offer. The SPN is built from the ground up to be superior to VPNs in every aspect - in regards to privacy.
|
||||
|
||||
<br>
|
||||
<br>
|
||||
## Part 2: Technical Deep-Dive Comparison
|
||||
|
||||
---
|
||||
|
||||
<br>
|
||||
<br>
|
||||
|
||||
Want to know more? Let's dive even deeper...
|
||||
If you are the curious, explore more technical details in the additional write-up below:
|
||||
|
||||
{% include spn_vs_vpns_tech.html %}
|
||||
|
||||
|
|
@ -137,28 +135,26 @@ Want to know more? Let's dive even deeper...
|
|||
|
||||
VPNs (Virtual Private Networks) are, well, networks that carry data packets through a tunnel from one point to the next. They are a more or less seamless part of the network. Packets destined for the Internet go into the VPN and out again without change. This means that packets are just relayed somewhere else and do not receive any advanced protection. Multi-Hop VPNs just relay your packets via one more server, but the problem remains: The packets do not receive any extra protection. Every server in that Multi-Hop chain can see all your traffic. Yes, the last server cannot see your IP address, but the previous servers can see all your traffic unencrypted and log everything you do. Oh, and just hope that your VPN client does not log into the last server in the chain too, then it even might have your VPN login data and again know who you are.
|
||||
|
||||
Instead of just doing some tricks with packet routing, the SPN protects your traffic and identity with proper cryptography. Every packet is end-to-end encrypted to every single server along the chain of servers the connection uses. This was originally invented for Tor and was called [Onion Routing](https://en.wikipedia.org/wiki/Onion_routing). This way, every server in the chain only knows the previous and the next hop. No server ever knows who you are _and_ where you are going to.
|
||||
Instead of just doing some tricks with packet routing, the SPN protects your traffic and identity with proper cryptography. Every packet is end-to-end encrypted to every single server along the chain of servers the connection uses. This was originally invented for Tor and is called [Onion Routing](https://en.wikipedia.org/wiki/Onion_routing). This way, every server in the chain only knows the previous and the next hop. No server ever knows who you are _and_ where you are going to.
|
||||
|
||||
|
||||
|
||||
But the SPN goes even one step further. Instead of using your username and password - which makes you identifyable - to log into the SPN, Portmaster authenticates itself not against the network itself, but against the SPN Account Service, which verifies you are allowed to access the network. It then give you special cryptographically blinded tokens, which prove your access permission, but are not linked to your account anymore. <span class="emphasize">This way, no server in the SPN will ever know your username.</span>
|
||||
But the SPN goes even one step further. Instead of using your username and password - which makes you identifiable - to log into the SPN, Portmaster authenticates itself not against the network itself, but against the SPN Account Service, which verifies you are allowed to access the network. It then give you special cryptographically blinded tokens, which prove your access permission, but are not linked to your account anymore. <span class="emphasize">This way, no server in the SPN will ever know your username.</span>
|
||||
|
||||
### Node Ownership and Logging
|
||||
|
||||
As VPNs are centralized, all their servers are operated by only one entity - the VPN provider itself. They can, therefore, monitor all you traffic and see what you are up to. This is why they tout their "No Logging" policies so loudly, because they know they can see everything.
|
||||
|
||||
The SPN, on the other hand, invites the community to join the network and strengthen it by adding diversity to the operators of the network. This way - in addition to the cryptographic protections - it is made almost impossible that anyone will ever be able to track you through the SPN. Also, because of the cryptographic identity protection before, there are not even any logs with identifiable data to begin with!
|
||||
SPN on the other hand invites the community to join the network and strengthen it by adding diversity to the operators of the network. This way - in addition to the cryptographic protections - it is made almost impossible that anyone will ever be able to track you through the SPN. Also, because of the cryptographic identity protection mentioned before, there are not even any logs with identifiable data to begin with!
|
||||
|
||||
Side note: Community nodes will be compensated in some form in the future.
|
||||
|
||||
### No Kill Switch Needed
|
||||
### SPN Does Not Need A Kill Switch
|
||||
|
||||
VPNs came up with the idea of kill switches, because they need to change the "default route", which is more or less what tells your device where to send all its traffic to.
|
||||
If you install a VPN, it will add a "virtual network" to your device and will update the default route to point to that network. If your device sends network packets to that virtual network, they will be encrypted and sent to your VPN provider, who will then release these packets to the Internet to do their thing. So far so good.
|
||||
|
||||
But when (not if) the connection to your VPN provider breaks - for whatever reason - your operating system will disable the virtual network and automatically change the default route to point to your ISP. This happens in a blink of an eye - your VPN software will not even notice.
|
||||
|
||||
The SPN is part of Portmaster, which tightly controls all the network connections of your device. It always knows what is going on and stops any leaks in its tracks.
|
||||
SPN easily solves this since it is part of Portmaster, which tightly controls all the network connections of your device. It always knows what is going on and stops any leaks in its tracks.
|
||||
|
||||
### Private Account and Payments
|
||||
|
||||
|
|
@ -169,4 +165,4 @@ While there are VPN providers that offer very good options in this area, many of
|
|||
When you sign up for the SPN, you can just go with the pre-filled random generated username and choose a password. You need to fill out a country with a matching phone prefix for tax and legal reasons - just to make everything legal and well on our side. While we cannot verify what you fill in these fields - we do not look at your IP address - we trust that our users are well-meaning and trustworthy.
|
||||
|
||||
Payments can be done using Bitcoin, Ethereum and Monero as well as sending us cash (Euros) in a letter.
|
||||
If you do not need to protect your privacy in that regard, we offer credict card payments and PayPal for your convenience.
|
||||
If you do not need to protect your privacy in that regard, we offer credit card payments and PayPal for your convenience.
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue