mirror of
https://github.com/safing/web
synced 2025-09-01 10:39:03 +00:00
Fix typos and remove contractions
This commit is contained in:
parent
8201fba43d
commit
c359e6777b
1 changed files with 9 additions and 9 deletions
|
|
@ -54,7 +54,7 @@ With this mindest, let's dig into the details.
|
|||
|
||||
### Multiple Identities
|
||||
|
||||
Open any VPN app, and you are presented with your most important choice: Choose the country you want to browse the Internet from. You exchange the identity of being a customer of your ISP with the identity of being a customer of your VPN provider. This is good if you trust your VPN more than your ISP, but it won't fool many trackers.
|
||||
Open any VPN app, and you are presented with your most important choice: Choose the country you want to browse the Internet from. You exchange the identity of being a customer of your ISP with the identity of being a customer of your VPN provider. This is good if you trust your VPN more than your ISP, but it will not fool many trackers.
|
||||
|
||||
This is how this looks like:
|
||||
|
||||
|
|
@ -83,7 +83,7 @@ Needless to say, VPNs cannot do this automatically, as they can only use one "ex
|
|||
|
||||
While there are some VPNs that are able to exclude the local network (LAN) or certain apps from the VPN, the SPN takes this to a new level.
|
||||
|
||||
Similar to firewall rules, you can very easily exclude any combination of connections from being routed through the SPN. By default, it excludes local network resources, as well as any captive portal. You don't need to turn it off to log into the WiFi when traveling!
|
||||
Similar to firewall rules, you can very easily exclude any combination of connections from being routed through the SPN. By default, it excludes local network resources, as well as any captive portal. You do not need to turn it off to log into the WiFi when traveling!
|
||||
|
||||
### Easy Setup
|
||||
|
||||
|
|
@ -111,11 +111,11 @@ Only later companies started to offer a "VPN" as an online privacy solution for
|
|||
|
||||
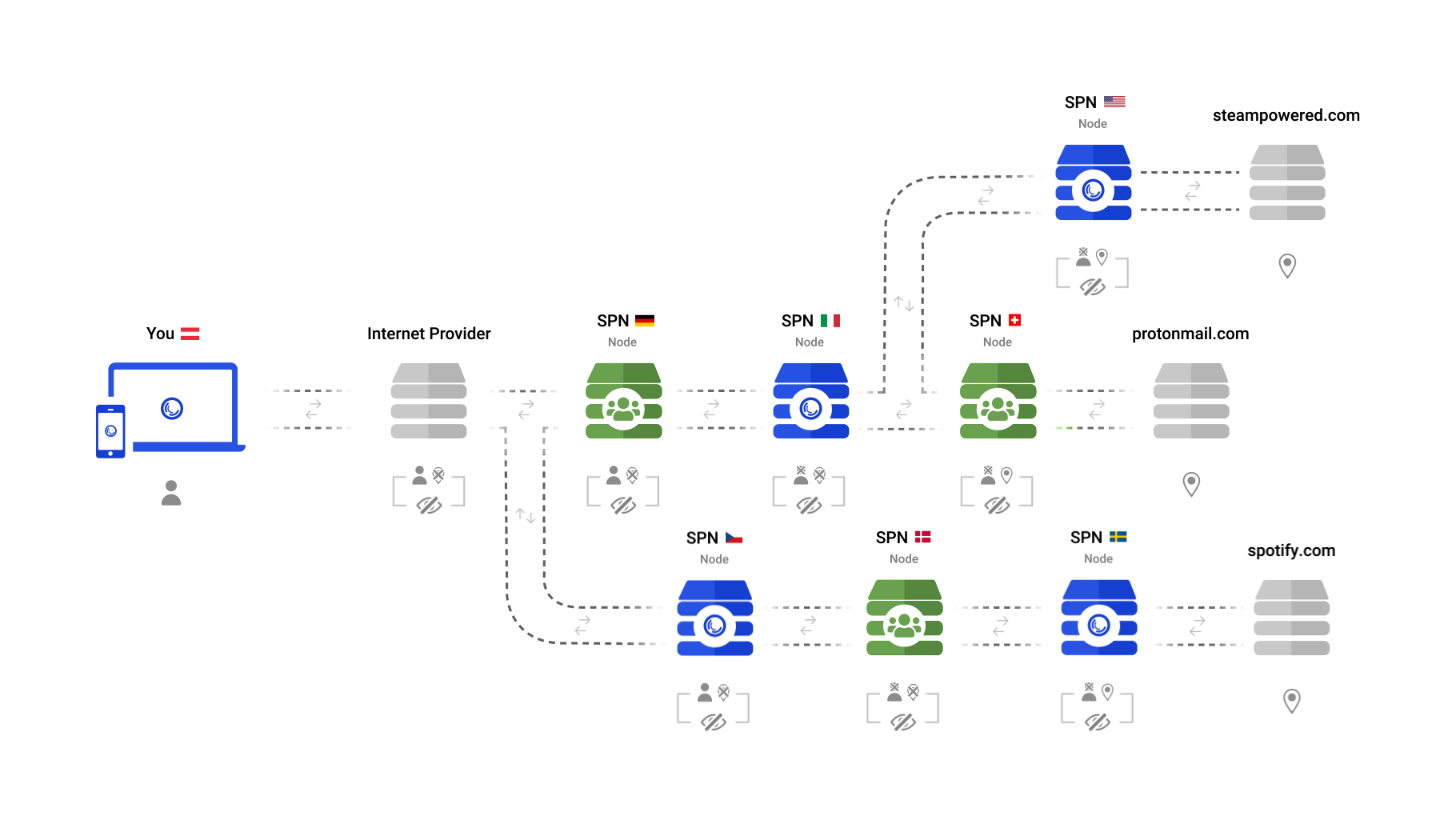
The SPN does not have IP or DNS leaks, because it is part of Portmaster, the privacy firewall that is in control of all your connections.
|
||||
|
||||
The SPN does not need a kill switch and it does not need "No Log Policies", because all traffic goes through multiple servers and is encrypted in layers. This means that no server ever knows both who you are (ie. your IP address) and where you are going to (ie. the website you are visiting).
|
||||
The SPN does not need a kill switch and it does not need "No Log Policies", because all traffic goes through multiple servers and is encrypted in layers. This means that no server ever knows both who you are (ie. your IP address) and where you are going to (ie. the website you are visiting).
|
||||
|
||||
|
||||
|
||||
The SPN does one thing and it's very good at it: Protecting your privacy.
|
||||
The SPN does one thing and it is very good at it: Protecting your privacy.
|
||||
|
||||
### Conclusion: SPN is a better fit for most threat models
|
||||
|
||||
|
|
@ -135,7 +135,7 @@ Want to know more? Let's dive even deeper...
|
|||
|
||||
### Cryptographic Identity Protection
|
||||
|
||||
VPNs (Virtual Private Networks) are, well, networks that carry data packets through a tunnel from one point to the next. They are a more or less seamless part of the network. Packets destined for the Internet go into the VPN and out again without change. This means that packets are just relayed somewhere else and do not receive any advanced protection. Multi-Hop VPNs just relay your packets via one more server, but the problem remains: The packets do not receive any extra protection. Every server in that Multi-Hop chain can see all your traffic. Yes, the last server can't your IP address, but the previous servers can see all your traffic unencrypted and log everything you do. Oh, and just hope that your VPN client does not log into the last server in the chain too, then it even might have your VPN login data and again know who you are.
|
||||
VPNs (Virtual Private Networks) are, well, networks that carry data packets through a tunnel from one point to the next. They are a more or less seamless part of the network. Packets destined for the Internet go into the VPN and out again without change. This means that packets are just relayed somewhere else and do not receive any advanced protection. Multi-Hop VPNs just relay your packets via one more server, but the problem remains: The packets do not receive any extra protection. Every server in that Multi-Hop chain can see all your traffic. Yes, the last server cannot see your IP address, but the previous servers can see all your traffic unencrypted and log everything you do. Oh, and just hope that your VPN client does not log into the last server in the chain too, then it even might have your VPN login data and again know who you are.
|
||||
|
||||
Instead of just doing some tricks with packet routing, the SPN protects your traffic and identity with proper cryptography. Every packet is end-to-end encrypted to every single server along the chain of servers the connection uses. This was originally invented for Tor and was called [Onion Routing](https://en.wikipedia.org/wiki/Onion_routing). This way, every server in the chain only knows the previous and the next hop. No server ever knows who you are _and_ where you are going to.
|
||||
|
||||
|
|
@ -147,16 +147,16 @@ But the SPN goes even one step further. Instead of using your username and passw
|
|||
|
||||
As VPNs are centralized, all their servers are operated by only one entity - the VPN provider itself. They can, therefore, monitor all you traffic and see what you are up to. This is why they tout their "No Logging" policies so loudly, because they know they can see everything.
|
||||
|
||||
The SPN, on the other hand, invites the community to join the network and strengthen it by adding diversity to the operators of the network. This way - in addition to the cryptographic protections - it is made almost impossible that anyone will ever be able to track you through the SPN. Also, because of the cryptographic identity protection before, there aren't even any logs with identifyable data to begin with!
|
||||
The SPN, on the other hand, invites the community to join the network and strengthen it by adding diversity to the operators of the network. This way - in addition to the cryptographic protections - it is made almost impossible that anyone will ever be able to track you through the SPN. Also, because of the cryptographic identity protection before, there are not even any logs with identifiable data to begin with!
|
||||
|
||||
Side note: Community nodes will be compensated in some form in the future.
|
||||
|
||||
### No Kill Switch Needed
|
||||
|
||||
VPNs came up with the idea of kill switches, because they need to change the "default route", which is more or less what tells your device where to send all it's traffic to.
|
||||
VPNs came up with the idea of kill switches, because they need to change the "default route", which is more or less what tells your device where to send all its traffic to.
|
||||
If you install a VPN, it will add a "virtual network" to your device and will update the default route to point to that network. If your device sends network packets to that virtual network, they will be encrypted and sent to your VPN provider, who will then release these packets to the Internet to do their thing. So far so good.
|
||||
|
||||
But when (not if) the connection to your VPN provider breaks - for whatever reason - your operating system will disable the virtual network and automatically change the default route to point to your ISP. This happens in a blink of an eye - your VPN software won't even notice.
|
||||
But when (not if) the connection to your VPN provider breaks - for whatever reason - your operating system will disable the virtual network and automatically change the default route to point to your ISP. This happens in a blink of an eye - your VPN software will not even notice.
|
||||
|
||||
The SPN is part of Portmaster, which tightly controls all the network connections of your device. It always knows what is going on and stops any leaks in its tracks.
|
||||
|
||||
|
|
@ -166,7 +166,7 @@ For a truly private experience, it is not only important to protect connections,
|
|||
|
||||
While there are VPN providers that offer very good options in this area, many of them require payment methods that identify you to 100%.
|
||||
|
||||
When you sign up for the SPN, you can just go with the pre-filled random generated username and choose a password. You need to fill out a country with a matching phone prefix for tax and legal reasons - just to make everything legal and well on our side. While we can't verify what you fill in these fields - we do not look at your IP address - we trust that our users are well-meaning and trustworthy.
|
||||
When you sign up for the SPN, you can just go with the pre-filled random generated username and choose a password. You need to fill out a country with a matching phone prefix for tax and legal reasons - just to make everything legal and well on our side. While we cannot verify what you fill in these fields - we do not look at your IP address - we trust that our users are well-meaning and trustworthy.
|
||||
|
||||
Payments can be done using Bitcoin, Ethereum and Monero as well as sending us cash (Euros) in a letter.
|
||||
If you do not need to protect your privacy in that regard, we offer credict card payments and PayPal for your convenience.
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue